Cybersecurity Project: Nmap 7.80 vs 7.97
In the past few months, the venerable stalwart of the network scanning toolkit, Nmap, underwent a major version change from 7.80 to 7.97.
To compare these two versions of the software, I decided to do a network audit and compare the results via Diffchecker.com. To generate the nmap query, I consulted the Nmap documentation and Copilot, which resulted in this query:
nmap -sV -T4 -O -A -v -oX network_inventory.xml
This command tells Nmap to perform a very detailed and aggressive scan of a target network. Here’s what each part does:
-sV: This option tells Nmap to detect service versions. In other words, it examines the open ports to figure out which software (and the version of that software) is running on each one.
-T4: This adjusts the speed of the scan by using a faster timing template. It’s designed for networks that are reliable, making the scan quicker while still aiming to be thorough.
-O: With this flag, Nmap attempts to detect the operating system running on the target machine(s) by analyzing characteristics of the responses.
-A: This is an all-in-one aggressive scan option. It not only includes OS detection and version detection but also runs additional scripts and conducts a traceroute to gather even more information about the network.
-v: The verbose option makes the output more detailed, giving you step-by-step feedback on what Nmap is finding as it runs.
-oX network_inventory.xml: Finally, this tells Nmap to save all the scan results in XML format in a file named “network_inventory.xml”, which can be useful for further analysis or reporting.
In plain terms, this command thoroughly examines a network to identify open ports, the services running (and their versions), the operating system of the target machines, and additional network details—all while providing detailed output and saving the results in an XML file for later review.
As a control, the same query was used both times. Any differences will be due to time, network configuration changes (different IP assigments), or changes to Nmap behavior.
Table of Contents
Off the Top: Formatting Changes
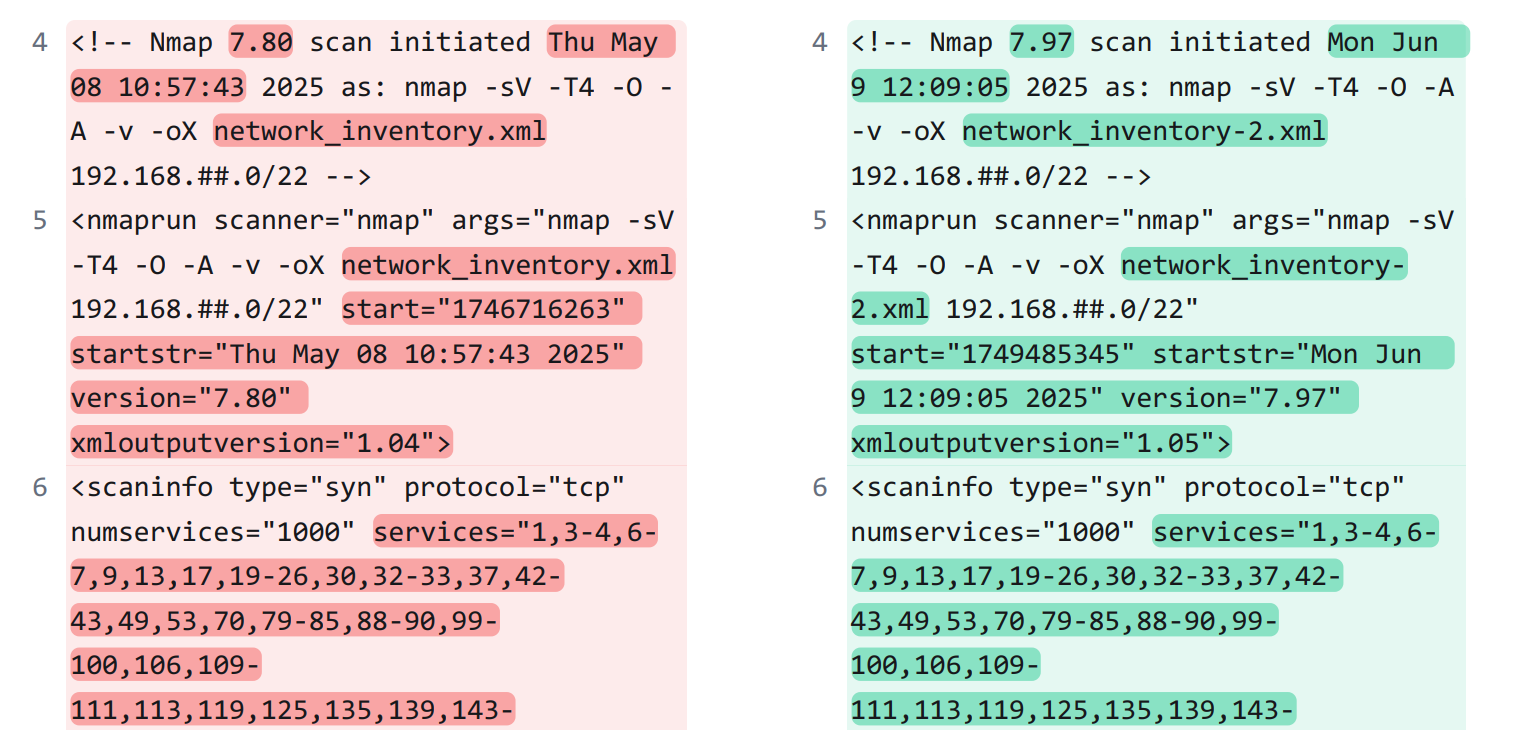
The start of the scan output is basically identical, aside from the obvious date and version number differences.
However, it is interesting to note the shift in date formatting, from 0# to #. This causes a subtle, but noticeable shift in how the Nmap query is presented.
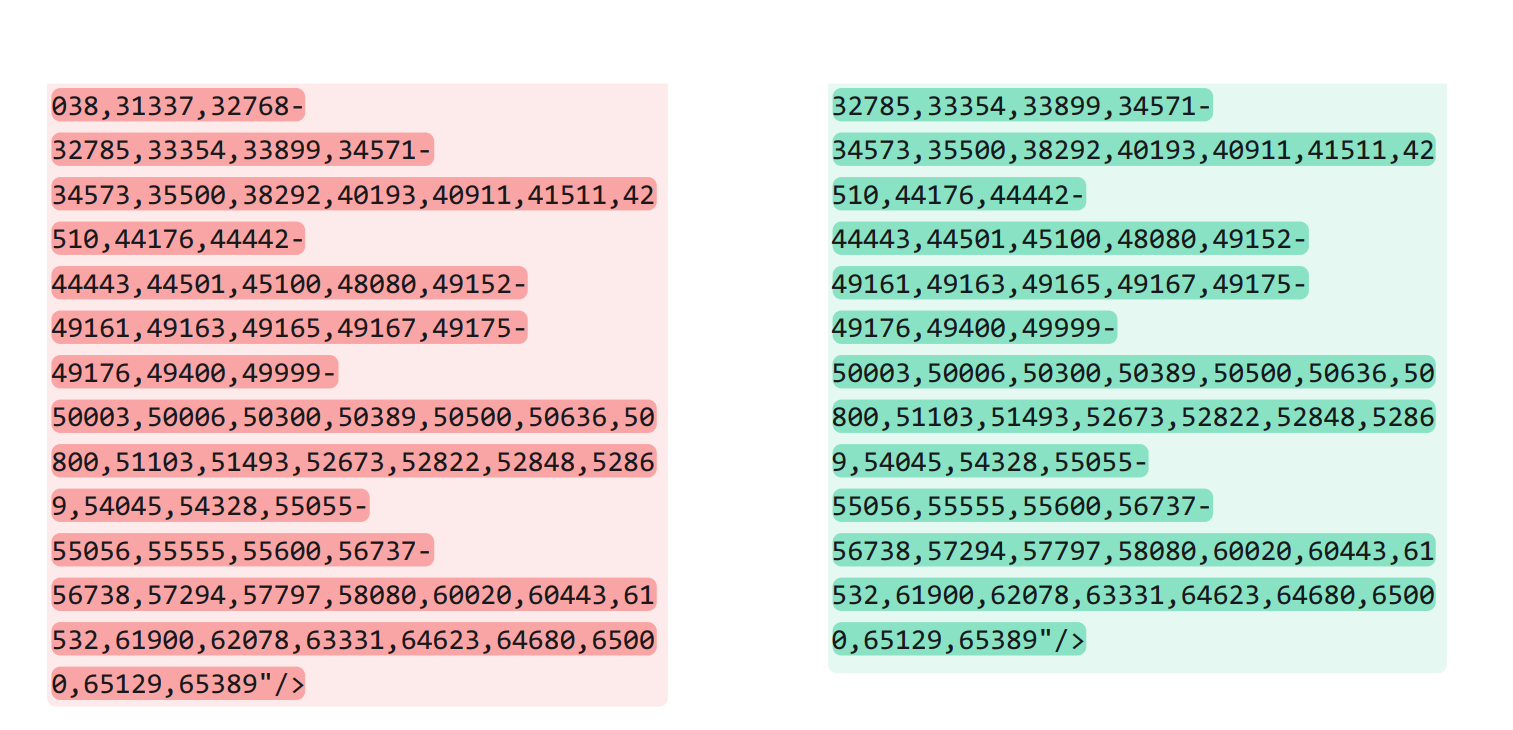
Oddly, the scan of TCP services for the newer version was shorter, despite covering the same number of services (1000). Looking through the scan revealed the point where a formatting change affected the list's length:
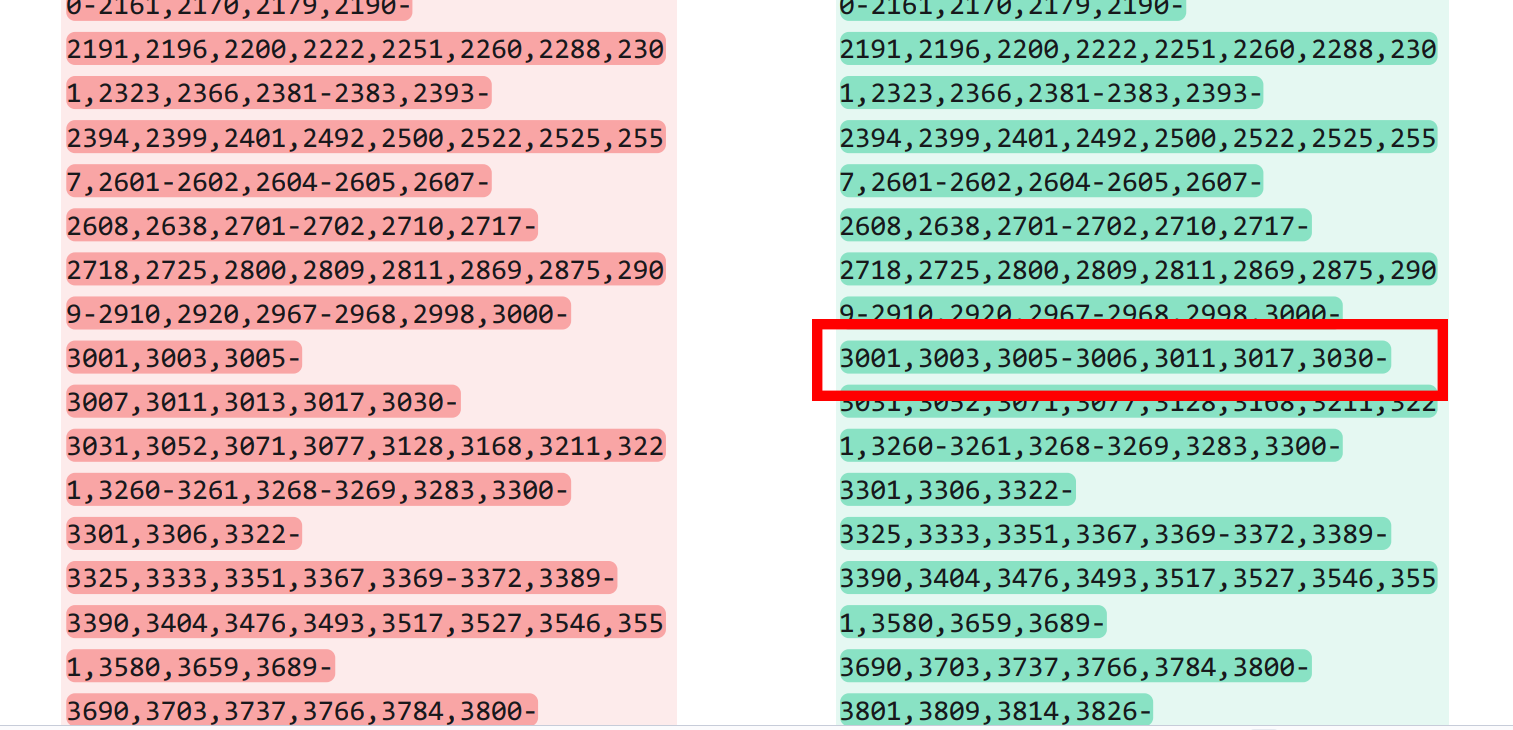
As far as I can determine, changing a range from 3005-3007 to 3005-3006 caused a wrapping change that partly compacted the list, and shifted up the end by one line.
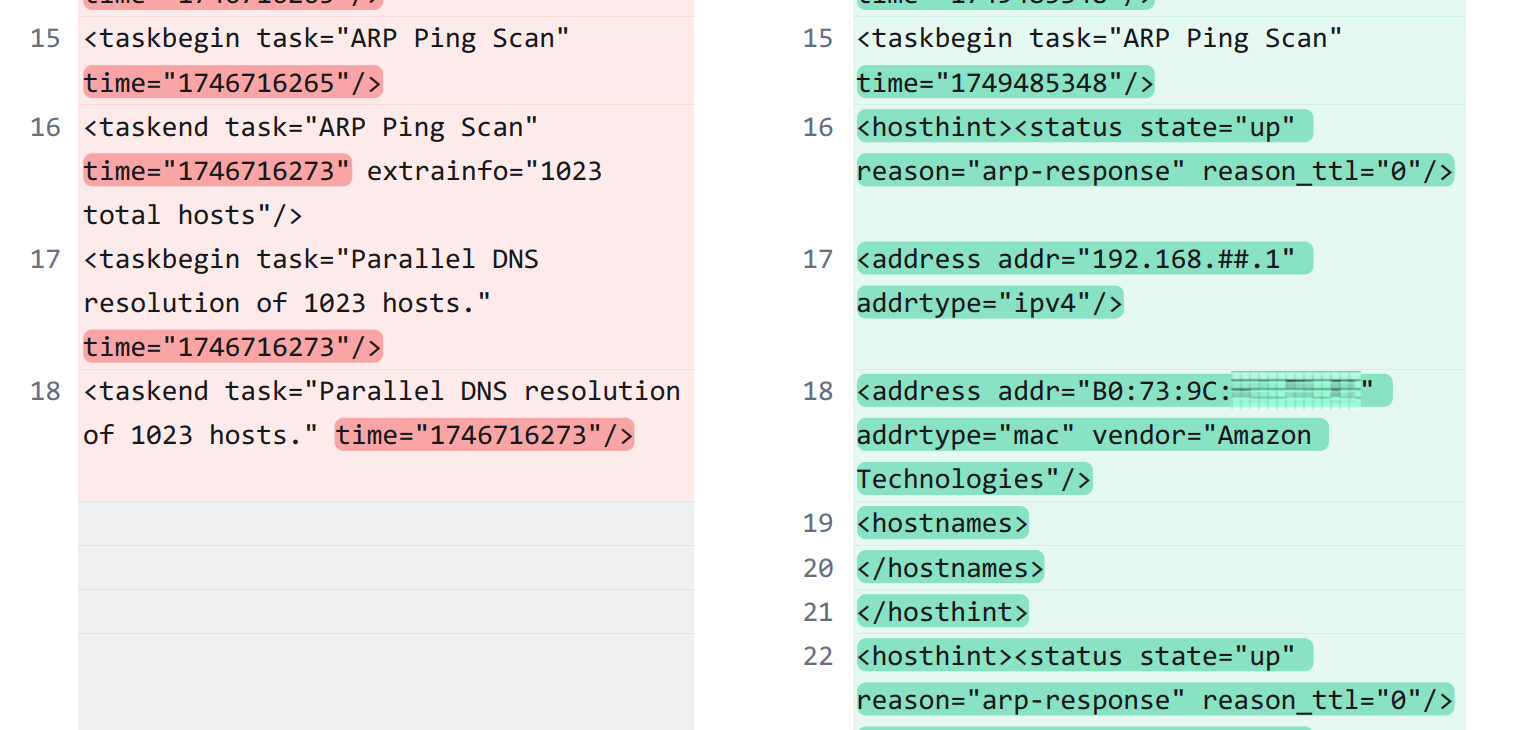
ARP Ping Scan is More Useful
One massive change is the utility of the base ARP Ping Scan function:
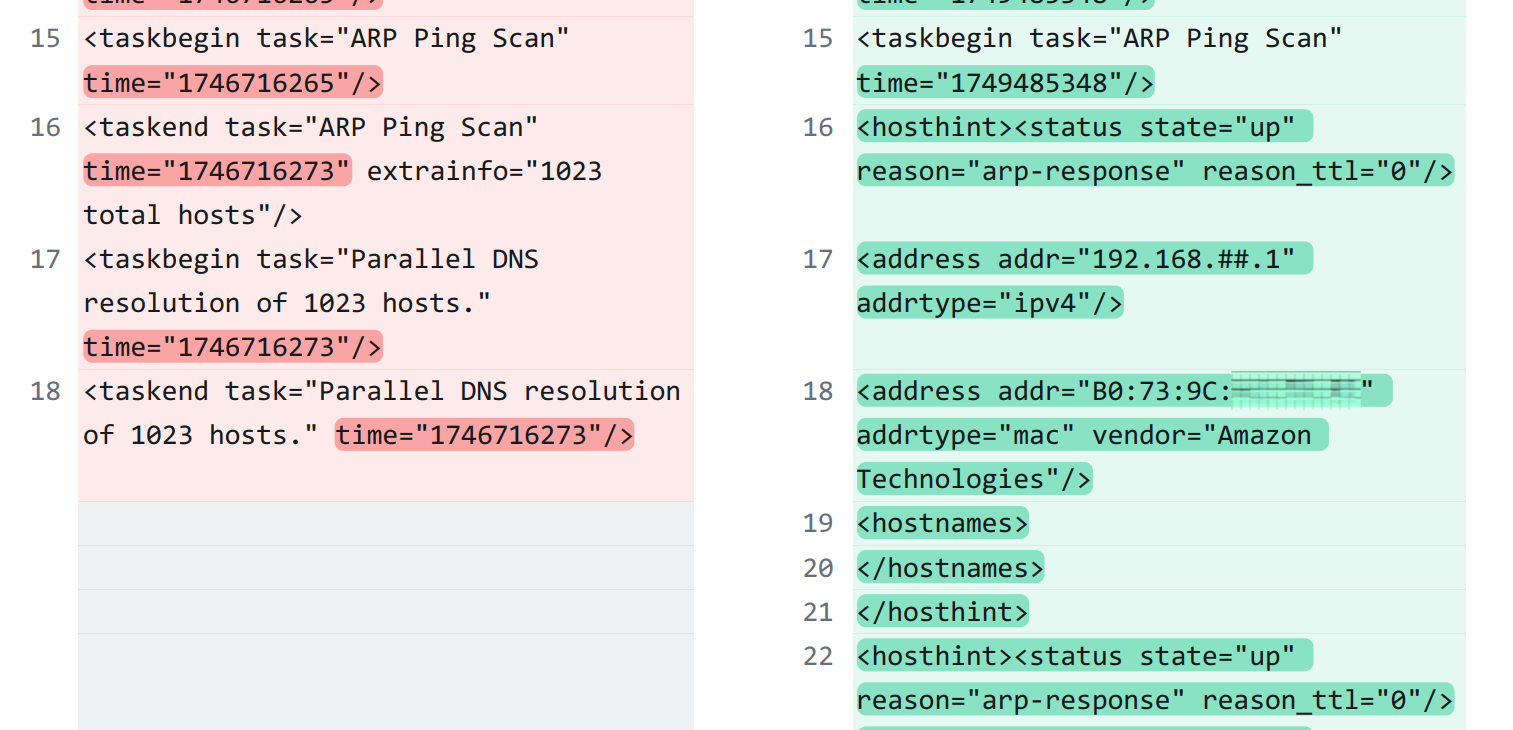
Nmap 7.97 (on the right) has something that used to be called on a separate command (-R): hostname resolution. This association of IP/MAC addresses with a hardware identifier early in the results is especially useful, given how long a scan output might be.
For example, the PDF version of the Diffchecker comparison of the two scan results is 263 results, and this is with a non-detailed (but verbose) scan.
The inclusion of the hostname resolutions in the output is less useful for people interacting with the Zenmap GUI, but for those who only interact with the Nmap command line interface (CLI) tool and its output, it is a major quality of life improvement.
SYN Stealth Scan Has More Ports
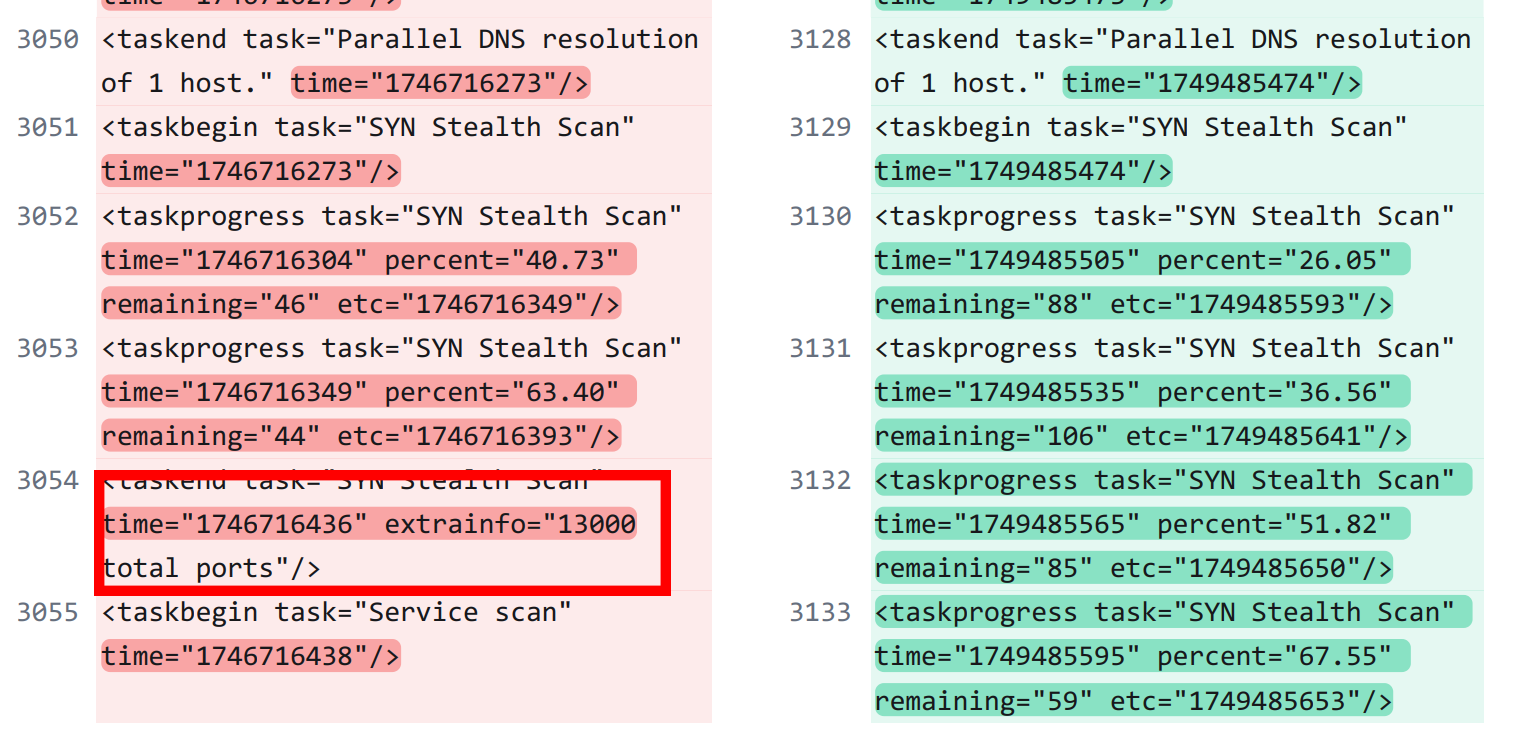
Another change between the two versions of Nmap is how long it takes to conduct a Syn Stealth scan. In 7.80, it only takes two progress reports to complete the scan. In 7.97, it takes five.
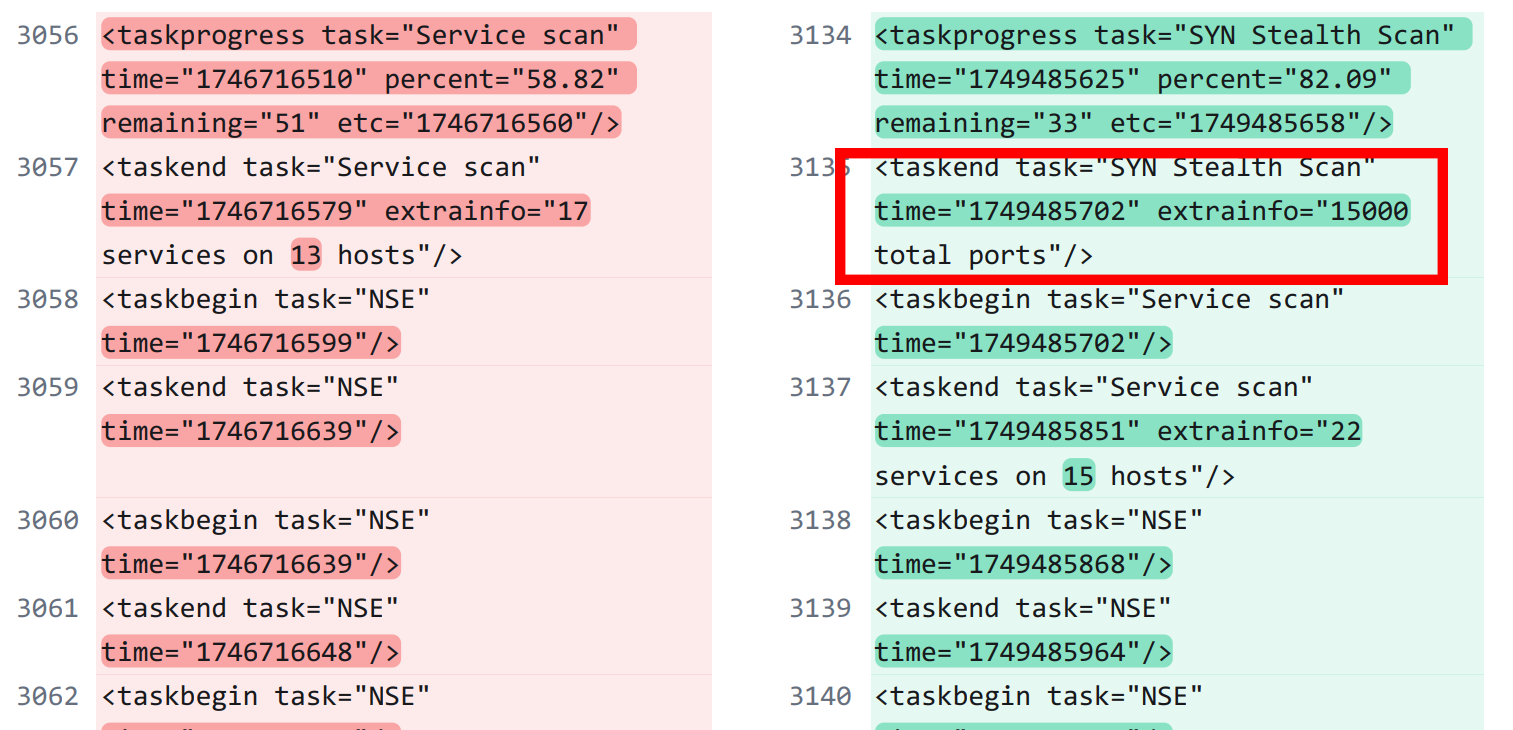
This seems related to the 2000 port increase from 7.80 to 7.97, although it is odd that 7.97 reports going from 88 remaining ports(?) to 106 at one point, indicating a possible bug.
ARP Response is More Detailed
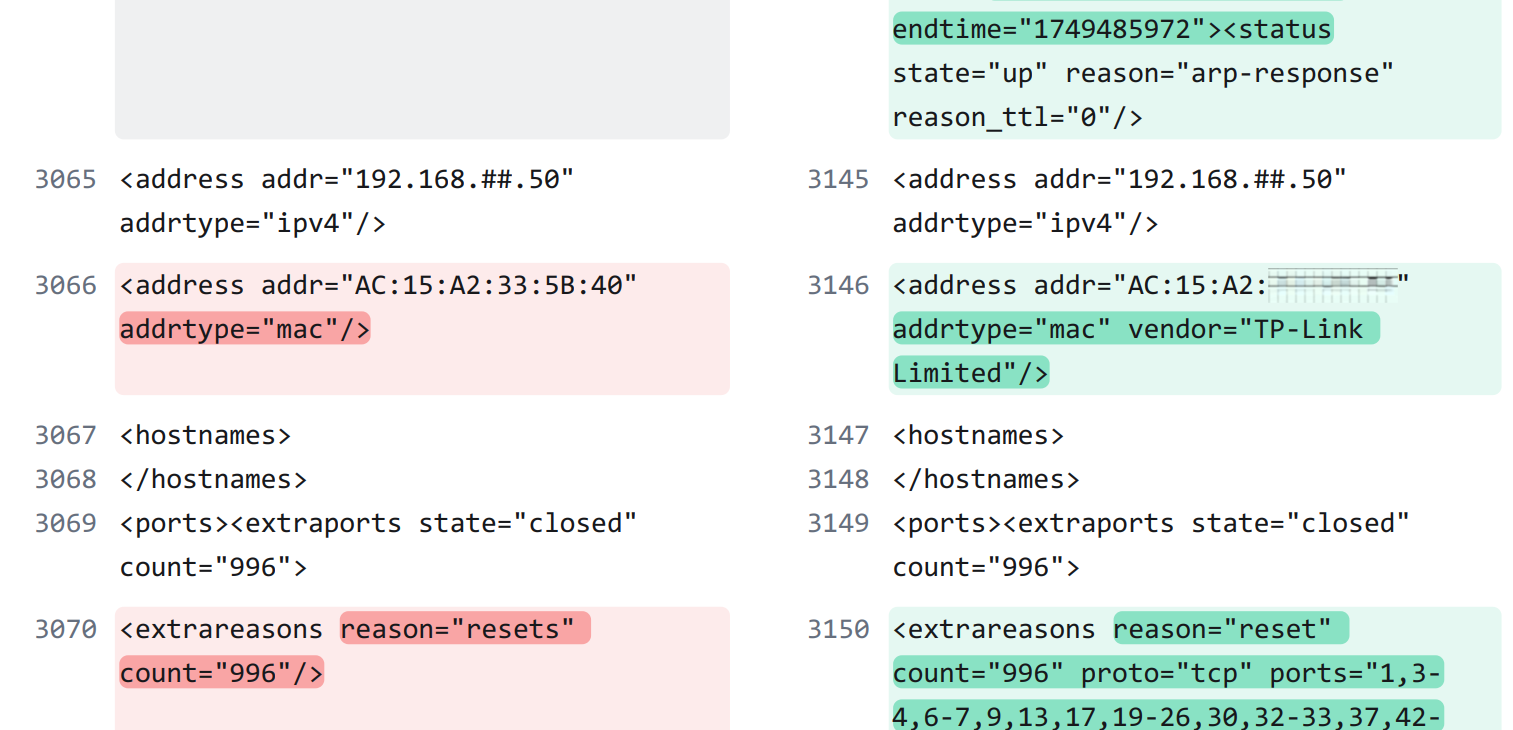
Another subtle improvement in the ARP response in 7.97 reporting for individual devices is the inclusion of a vendor ID.
This is most useful for identifying network devices, as the Network Interface Card will have a higher probability of reporting the name of the device's vendor. For other devices, such as computers, it may report the name of the network device vendor, which does not match the manufacturer/vendor name on the physical device. For example, a PC with an Intel wireless network card may be an Intel device... or a laptop from any number of vendors with an AMD processor and an Intel WiFi card.
The ARP response in 7.97 also goes through the full list of TCP ports that trigger a reset in the scan. This is valuable for an audit or when you want to understand the ports used by this specific scan, but it does bloat the size of the report.
Better, Concise HTTP Service Reporting
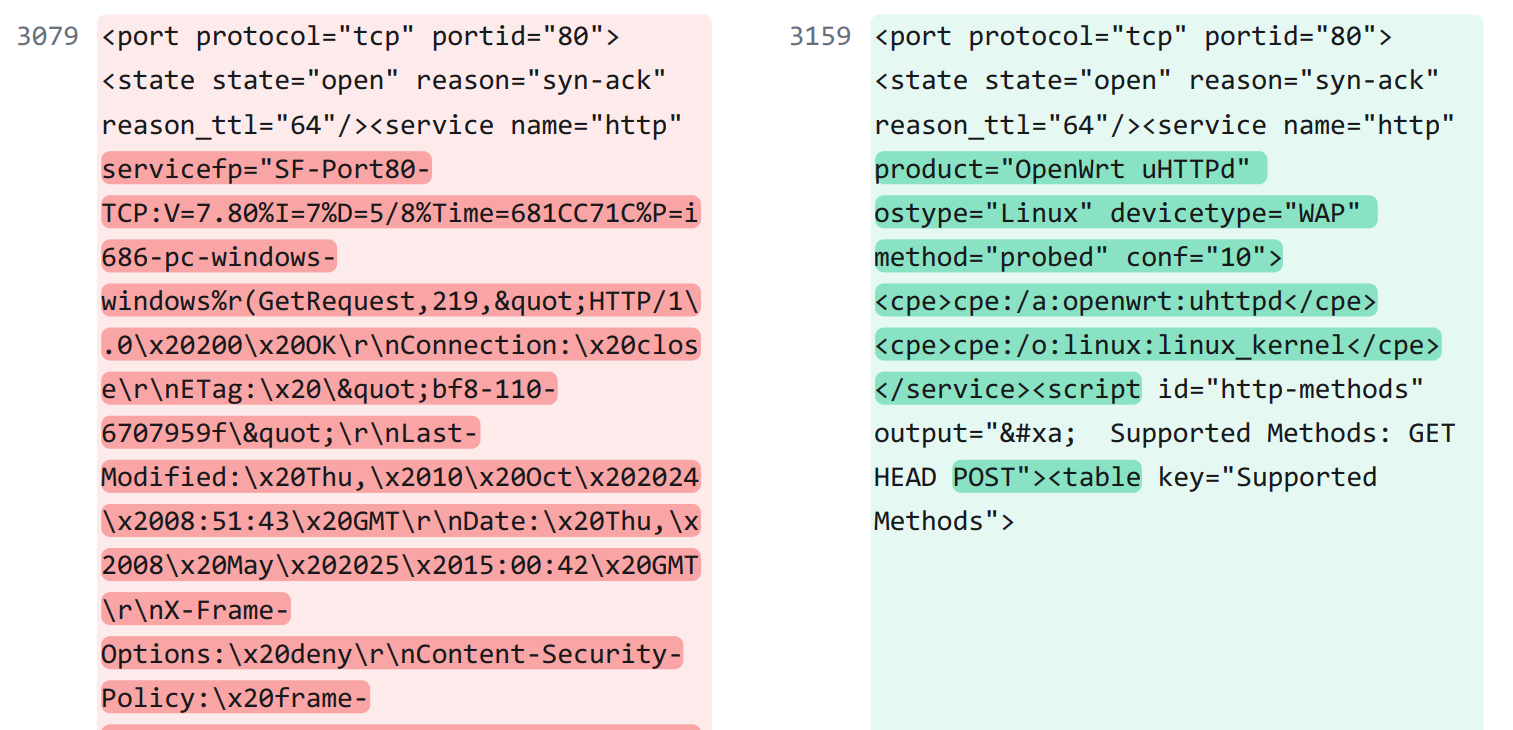
HTTP service reporting is much improved in 7.97, and is much more concise, but this seems to depend on the device and/or service in question. For example, the above image clearly shows that services on OpenWRT devices generate a condensed output of essential details of the device.
However, for other devices, like the Raspberry Pi in this next image, there is still a great deal of HTTP scraped data:
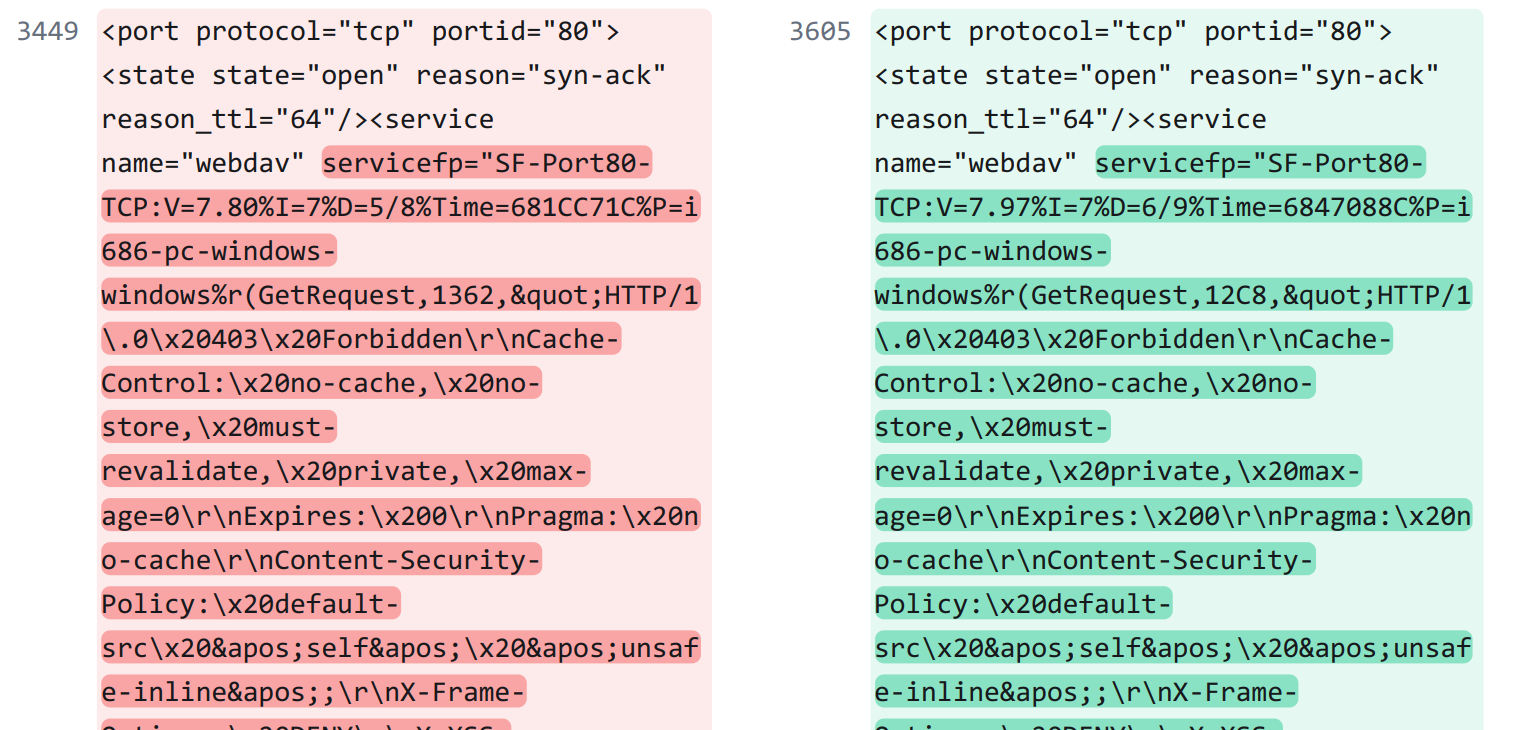
The main difference is that version 7.97's HTTP scraping is either much more efficient, or has been reworked to max out at a certain length. Lines 3505 to 3608 constitute the entirety of 7.97's output, but for 7.80, the same device's output is from lines 3449 to 3462. That's 3 lines versus 13, or a 76.92% decrease.
While this might be a downgrade for penetration testers and other exploitation focused roles, this is certainly an improvement for people who are just using Nmap to catalog what is on the network.
Overall, this simple test scenario merely scrapes the surface of the improvements made in Nmap 7.97, but it gives a good starting basis of comparison.

