Cybersecurity Project: Epic Games Store Packet Capture - Statistic Analysis
It's time to continue my grind through the data from the Epic Games Store packet capture! Since looking at encrypted packets wasn't providing many real insights, it's time to pivot statistics, courtesy of Wireshark!
Table of Contents
Conversations
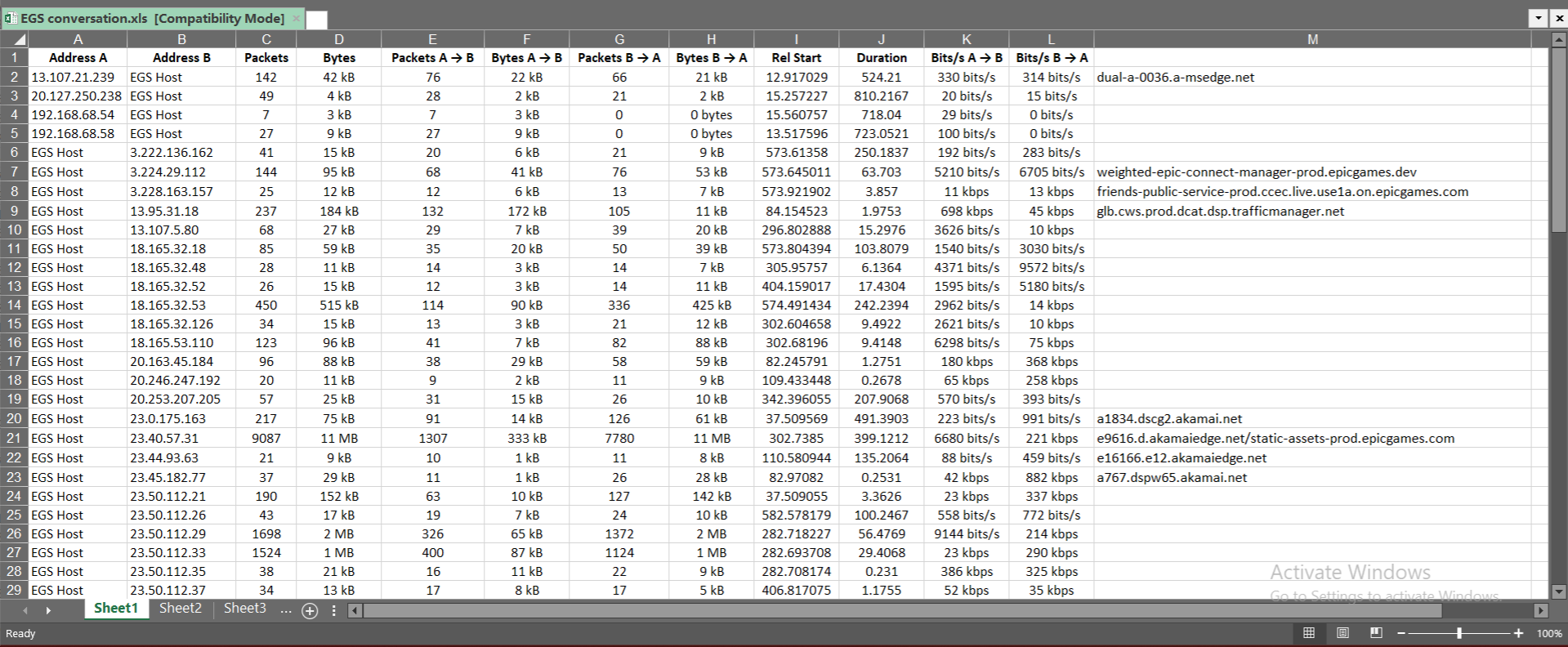
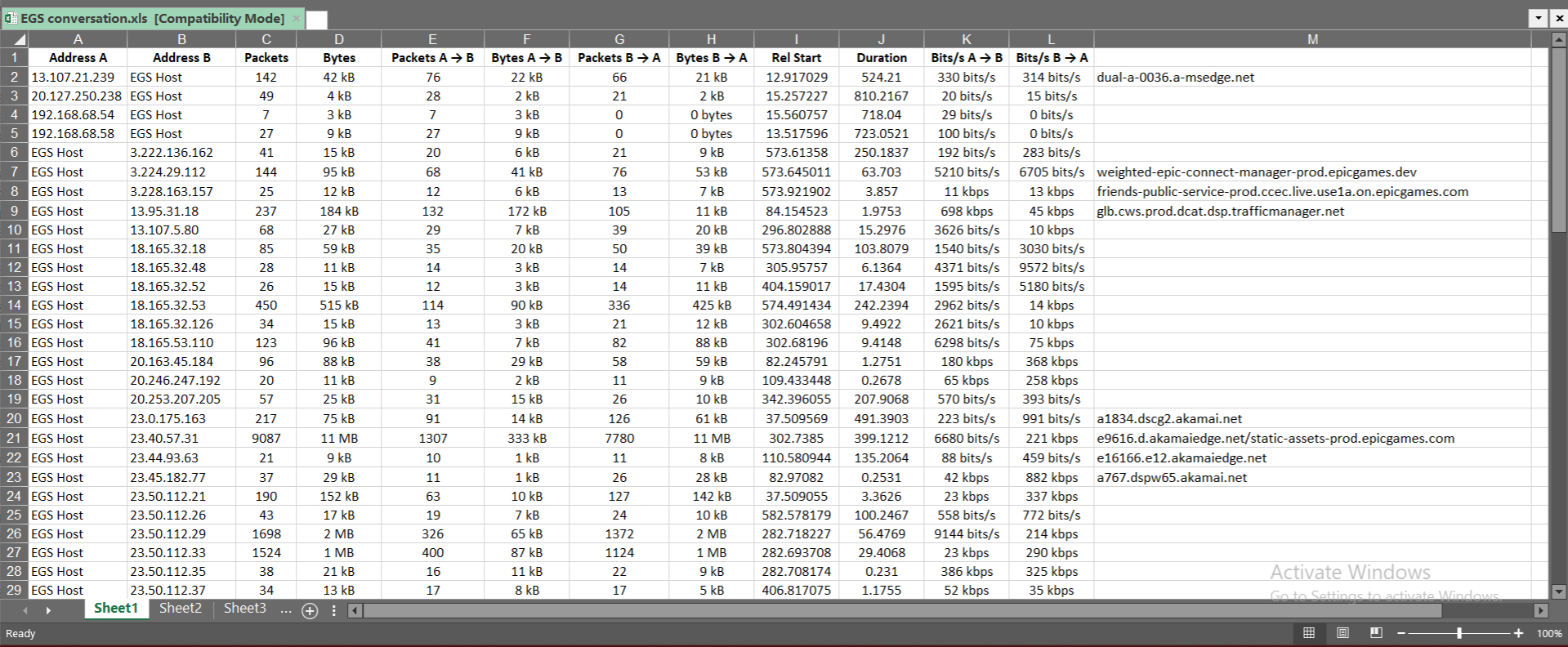
Under the Statistics options in Wireshark, Conversations is the fourth option, but possibly the most useful in terms of network flow analysis. The tool generates a table of the source/destination IPs, the total number of packets exchanged between them, the total bytes exchanged in the conversation, how many packets and bytes were exchanged in a specific direction, the relative start time of the conversation, the duration, and what the connection speed was in a specific direction.
You can export this table to a spreadsheet via copying as a CSV, which I did.
Why? Because if you remember earlier in this project, I generated a list of domains and the IPs associated with them. By copying the conversation data into the spreadsheet, I could then add the domains to those conversations, providing even greater context to my analysis.
This allowed me to see any outliers in the data, which weren't apparent when focusing on specific packet captures.
Insights
Here are some interesting highlights from the data:
| Address A | Address B | Packets | Bytes | Packets A → B | Bytes A → B | Packets B → A | Bytes B → A | Rel Start | Duration | Bits/s A → B | Bits/s B → A | Domain |
| EGS Host | 23.40.57.31 | 9087 | 11 MB | 1307 | 333 kB | 7780 | 11 MB | 302.7385 | 399.1212 | 6680 bits/s | 221 kbps | e9616.d.akamaiedge.net/static-assets-prod.epicgames.com |
For example, we have this connection, which is initially to the domain e9616.d.akamaiedge.net, then executes a client hello that results in a connection to static-assets-prod.epicgames.com. This then results in 11 megabytes of data getting transferred to the EGS Host system. Based on the name of the domain, there's a high probability that this was just a number of images shown in the EGS client, likely thumbnails and banner images.
| Address A | Address B | Packets | Bytes | Packets A → B | Bytes A → B | Packets B → A | Bytes B → A | Rel Start | Duration | Bits/s A → B | Bits/s B → A | Domain |
| EGS Host | 23.205.165.152 | 38879 | 54 MB | 3108 | 173 kB | 35771 | 54 MB | 306.18383 | 3.983 | 348 kbps | 108 Mbps | a1859.w27.akamai.net/epicgames-download1.akamaized.net |
Next, we have another connection to an Akamai domain that then hands off to an Epic Games server. It is much less clear what this could be, given the encrypted nature of the contents. The small file size, compared to another EGS download, and the fact that I couldn't download anything through the Unreal Engine store leads me to believe that this might just be an EGS client update.
| Address A | Address B | Packets | Bytes | Packets A → B | Bytes A → B | Packets B → A | Bytes B → A | Rel Start | Duration | Bits/s A → B | Bits/s B → A | Domain |
| EGS Host | 146.75.126.33 | 598444 | 684 MB | 149461 | 9 MB | 448983 | 675 MB | 404.441049 | 273.8069 | 250 kbps | 19 Mbps |
This is an encrypted connection to fastly-download.epicgames.com, which is hosted on an AmazonS3 server. The 9 megabyte upload is highly suspicious, but the 675 megabyte download is also suspicious. However, if this was the initial EGS install/update, this might make some amount of sense.
(It does raise the question of why do you need over half a gigabyte of data for what's probably a browser. Even factoring in potential game dependencies like DirectX, C++, and .Net frameworks, it's a bit much.)
| Address A | Address B | Packets | Bytes | Packets A → B | Bytes A → B | Packets B → A | Bytes B → A | Rel Start | Duration | Bits/s A → B | Bits/s B → A | Domain |
| EGS Host | 104.18.50.190 | 2606571 | 3 GB | 779871 | 51 MB | 1826700 | 3 GB | 620.386146 | 216.3353 | 1903 kbps | 102 Mbps | cloudflare.epicgamescdn.com.cdn.cloudflare.net |
The most suspicious thing about this connection is not that it's moving several gigabytes of data - this is the main connection where Unreal Engine 4.26 was downloaded.
It's the fact that 51 megabytes were sent from my PC to the download server that's concerning. There's no logical reason why so much data would need to move from the client to the server.
However, I do have a possible theory.
Remember how there was a 54MB download from epicgames-download1.akamaized.net? That's close enough in size to the mysterious upload to be suspicious.
There's a possibility that the initial 54MB download was some kind of encapsulated authorization token, which was then decapsulated after download and reuploaded to authorize the download from the Unreal Engine store. Why you would do this is a mystery, because there's likely any number of more efficient methods to accomplish this same goal.
There's also a possibility that there was simply a million 54 byte ACK messages sent by my computer during the process. Unlike most of the other connections, this connection was only HTTP. Which makes sense - if you're going to be pushing tons of files, including many that are already compressed, adding encryption on top is not ideal.
(It does mean that I have nice list of filenames, hashes, and other data for various UE 4.26 components.)
Preliminary Takeaways
With so many of the captured packets being encrypted and lacking a good TLS inspection system to use for another round of packet capture, it's time to put this project to bed.
So, what are my main takeaways?
- AnyDesk is a good remote desktop solution within the confines of a home network.
- VirtualBox's lack of GPU pass through limits its utility as a tool for safely testing certain complex software that requires certain hardware features.
- Sandboxie-Plus could be a good method of testing potentially compromised/suspicious software for home labbers, but too many features require a paid license for it to be a great solution.
- Epic Games Store/Unreal Engine 4.26 may not behave properly when run in a basic Sandboxie configuration, making testing more difficult.
- EGS and Unreal Engine only run a handful of limited processes, so there doesn't appear to be any spyware in them, beyond telemetry that can be disabled via settings menus.
- Epic utilizes TLS for many of its internet connections to various servers, which is exemplary for security, but makes analysis of the actual traffic difficult without more advanced tools.
- Wireshark's lack of a built-in tool to quickly dump domains and their associated IPs is quite unfortunate, and hurts efforts by end users to help add to community generated domain block lists.
- In an investigation where you have a packet capture and no specific starting direction, the Conversations statistics generated by Wireshark can help identify IPs with traffic of interest.
- Once you have a list of domains and their associated IPs, run a Wireshark command prompt command to dump all the IPs captured in the packet, then run some kind of script to obtain all relevant IPs and associate them with the domains.
- EGS likes using Akamai domains as proxies/hosting for various servers, which does provide a bit of security via obscurity, but also leaves EGS potentially vulnerable to becoming a malware vector if the server is compromised.
- EGS winds up uploading a large amount of data while downloading files over long periods of time.
- 54 byte ACK packets can build up over the duration of the connection and lead up to multi-megabyte totals.
- Wireshark's Conversations statistics tool doesn't provide trend data, just overall totals and averages, which can be a bit misleading at first glance.
Now that this project's wrapped up, I'll be spending time on shorter cybersecurity topics while I prepare for the CompTIA Security+ exam. So keep an eye out for a wild range of topics in the near future!

