Cybersecurity Project: Epic Games Store Packet Capture - IPs 3
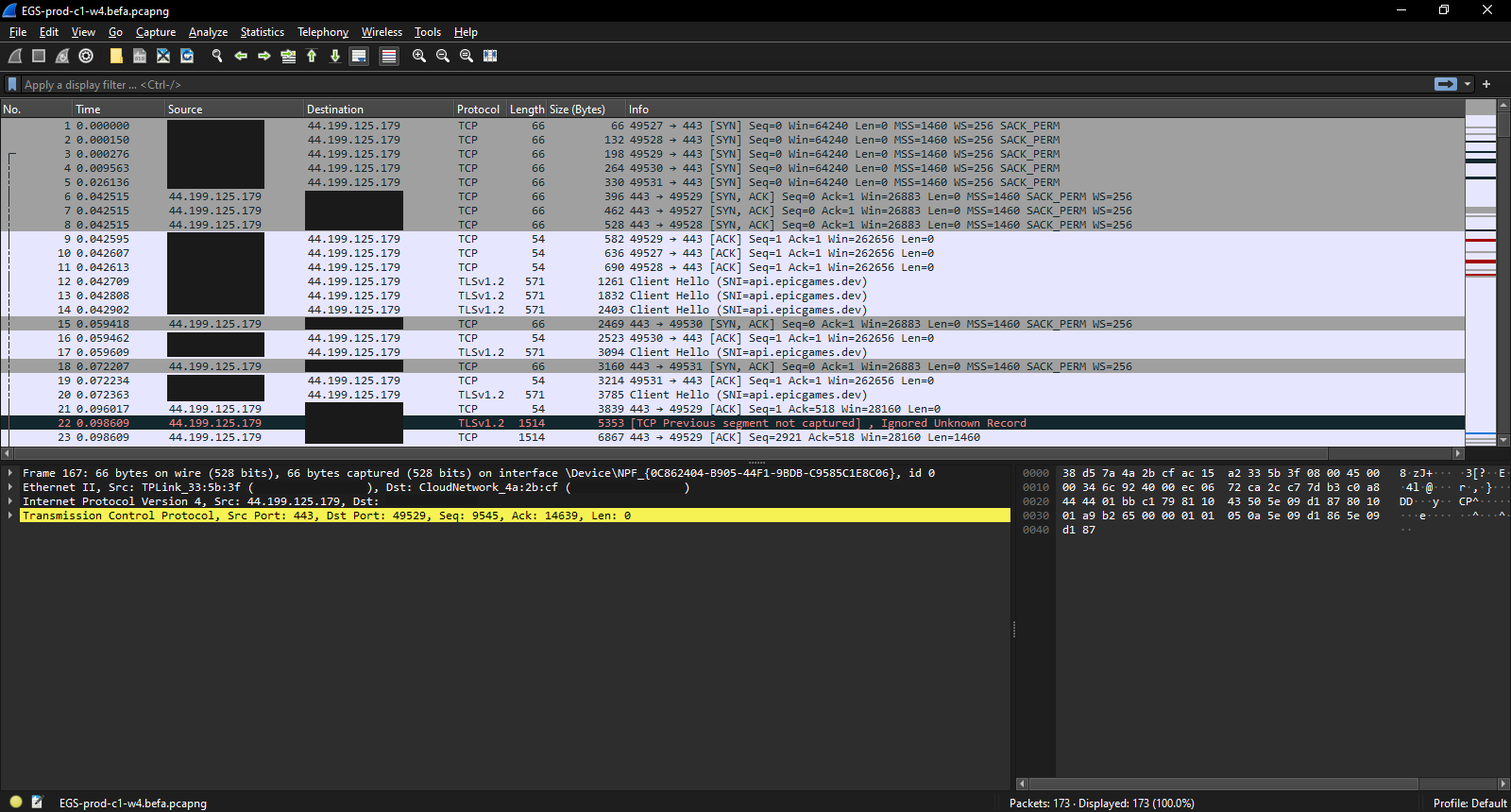
Getting back to the Epic Games Store investigation, it's time to look into another IP address from the packet capture.
We'll be looking at the largest capture packet for one IP address, which is targeting the eos-gateway-ingressv2-prod-c1-w4.befa.live.use1a.on.epicgames.c domain.
The Good Old 3-Way Handshake

The first and most obvious feature of this packet capture is the three way SYN/SYN-ACK/ACK handshake of a TCP connection. Since this is the start of the interaction with the domain/IP, this makes total sense and should be expected.
The next most interesting feature of this capture is the Client Hello. In this case, we're interacting with api.epicgames.dev, which indicates this connection has a high probability of being related to the Unreal Engine part of EGS. If my Raspberry Pi had more RAM (it only has 2GB), I would consider setting up a SIEM to monitor this specific connection and events related to it.
What is confusing without visibility into the contents of the packets is why there's multiple other three way handshakes after the initial one.
Lots of Server Hellos
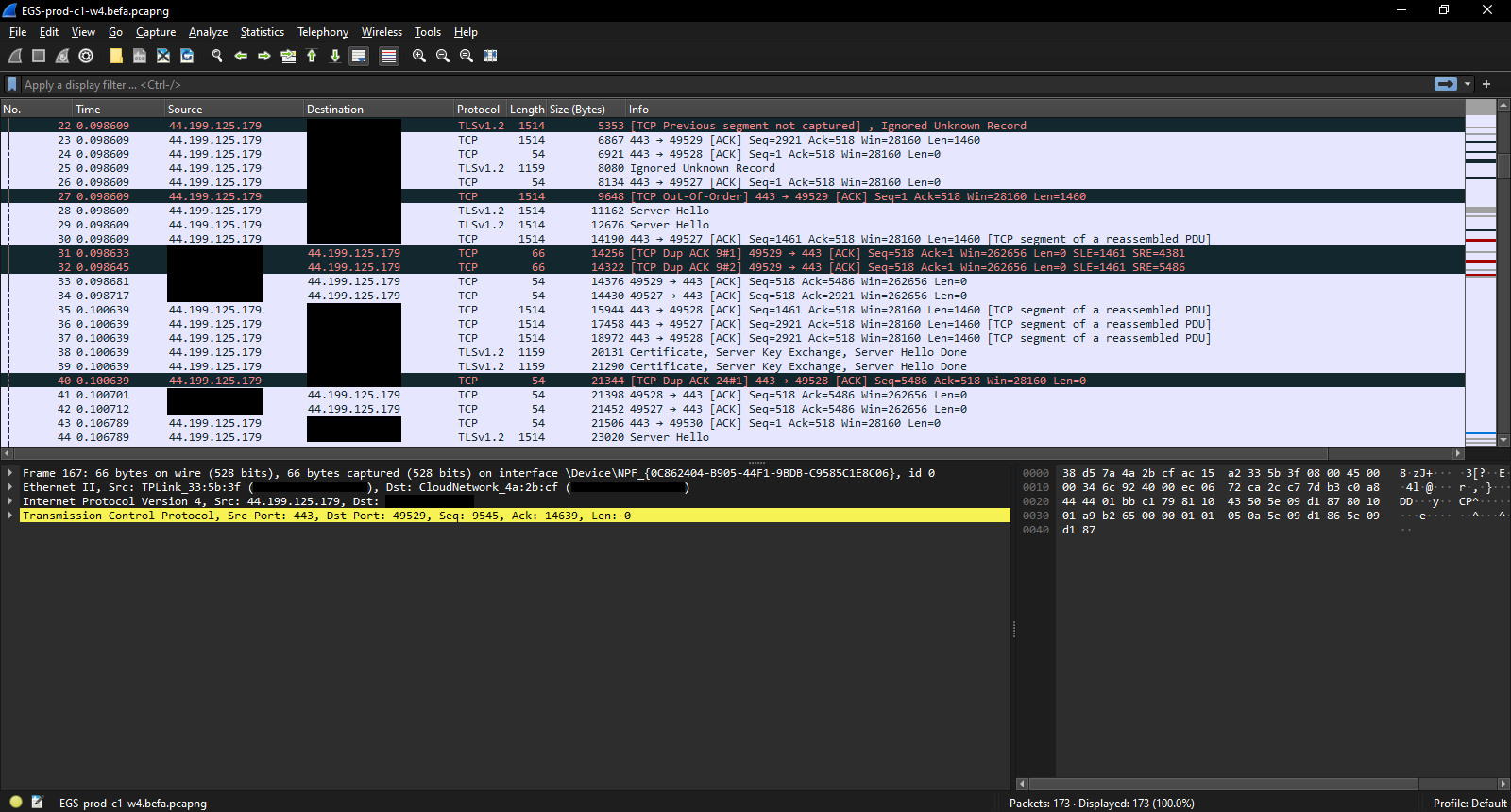
Curiously, more server hellos were given out. Scrolling down the packet capture gives a potential explanation:
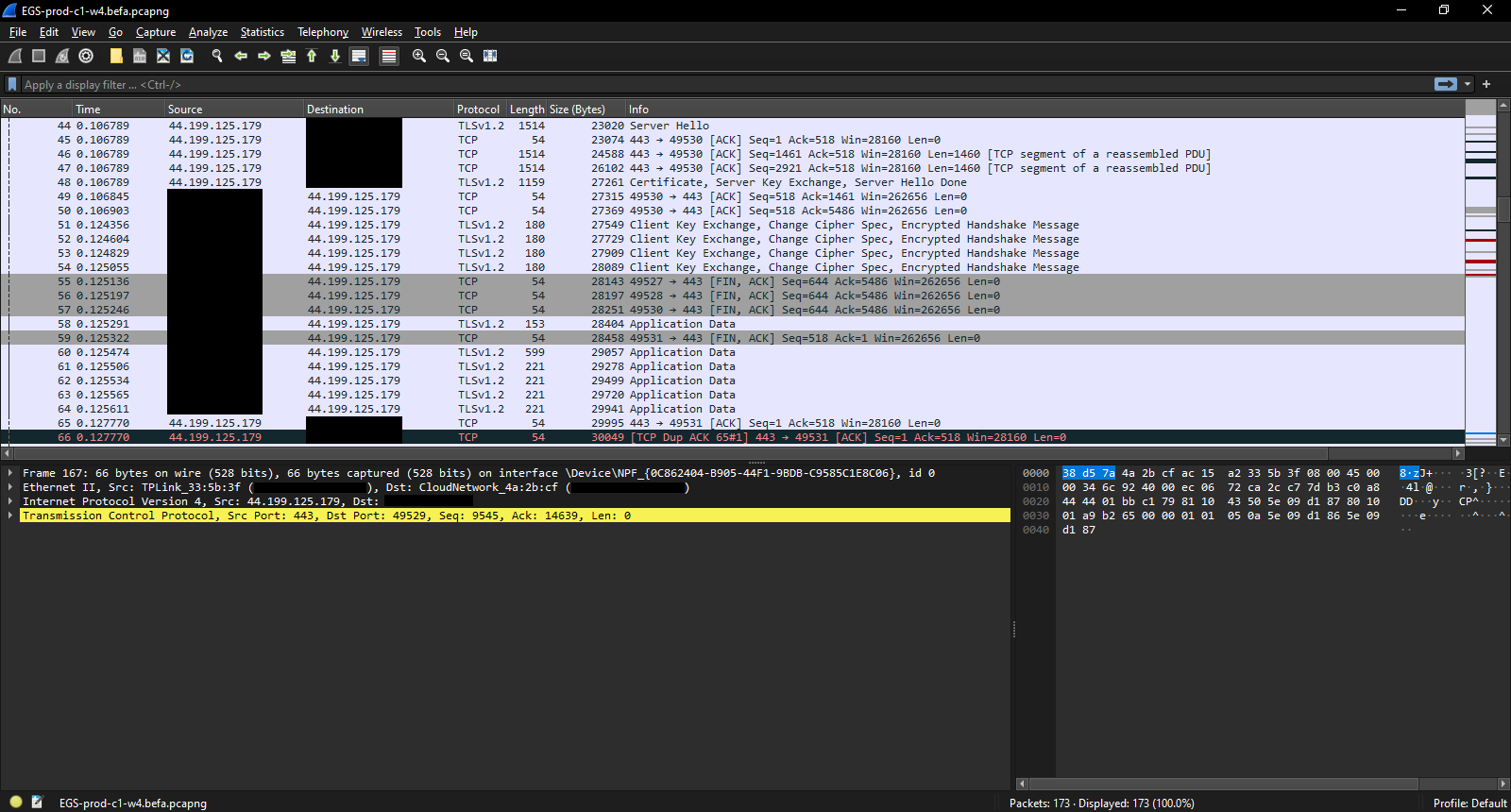
Some of these odd server hellos are almost certainly associated with initiating a connection to obtain the certificate and client key exchange. Once that was done, the connection with the client key server ended.
Unfortunately for this analysis, but generally comforting for EGS users, TLSv1.2 makes it impossible to actually see the contents of the packets.
Continuing further down the capture, we see another key exchange, and then an odd number of resets:
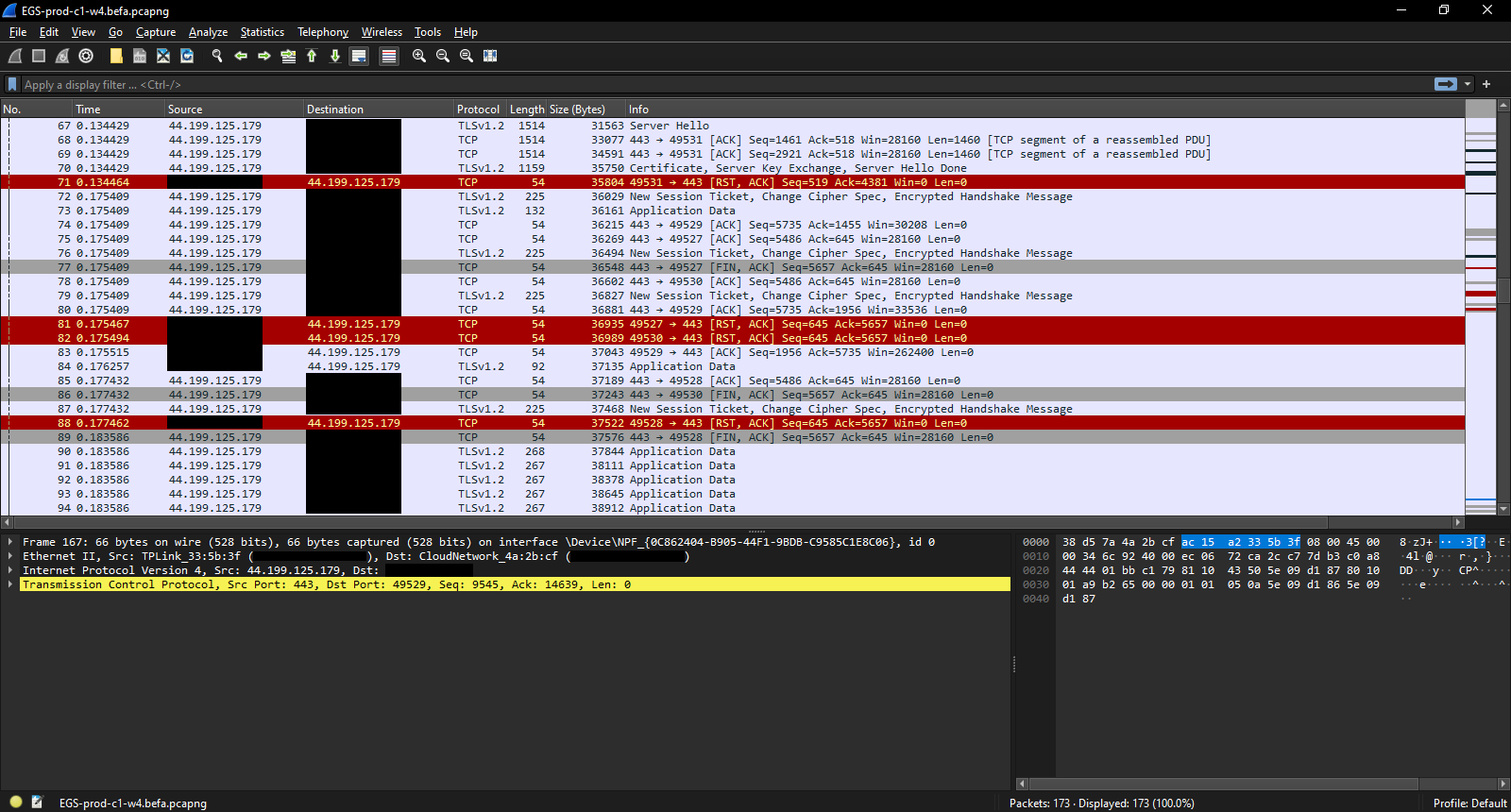
Without visibility into the packet contents, it's hard to figure out why the there are so many resets. It's possible that they correlate with bouncing around the Unreal Engine store or some other part of the login process.
We'll skip the massive amount of unreadable and ACK packets that made up the majority of this packet capture, and jump to the end. Here, we find something interesting - that communication between the client and server paused for 45 seconds, requiring a TCP Keep-Alive transmission.
Another 15 seconds after that, an encrypted alert seems to trigger the end of the connection with the FIN-ACK packets.
Future Research
Without any way to decrypt the packets, there's not much more that can be done with this IP address. However, the fact that this connection is associated with an Epic Games API means that it's well worth researching in the future. While the connection doesn't last long, the amount of traffic is quite surprising. There's definitely something worth looking into here, even if it just turns out to be an anonymized survey of the system's hardware.

