Cybersecurity Project: Epic Games Store Packet Capture - IPs 2
Last time, I began analyzing the Epic Games Store packet capture, looking for specific IPs associated with the domains I felt were suspicious or interesting.
It turns out that would be a more interesting challenge than I anticipate.
You Are Corr-Wrong!
The first domain I checked, account-public-service-prod03.ol.epicgames.com, had multiple IP addresses associated with it. Through sheer luck, I managed to find an IP address associated with while doing a manual search, and proceeded to analyze that traffic.
Since most of the other domains had multiple IPs as well, I decided to try using a script to find those IPs and save myself some time.
I started out this process by using Bing Copilot to help craft a PowerShell script to go through a list of the target domains, find any IP addresses associated with them, then output the list to a .txt file. This list would naturally include what domain was associated with the IP.
This perfectly functional PowerShell yielded no results, because PowerShell can't actually read the PCAPNG files, producing blank files.
After an embarrassing amount of time and effort, I realized the problem was that I needed to use Wireshark commands to export the IPs, then have a script filter them.
The Wireshark command was pretty simple, targeting ip.src, and using sort -u to isolate unique entries, before writing to a TXT file. I had to make a separate PCAPNG file, only containing packets with a frame length of 999 or less to get results within a reasonable time frame.
(Wireshark does not have a way to filter packets out by overall size, which is a major oversight, in my opinion.)
Once I had the final list of IPs, I created a PowerShell script (reusing chunks of code from the failed ones) that would go through the list and isolate the IPs I was looking for.
The final PowerShell script I used to filter is as follows:
# Specify the path to your input .txt file containing IP addresses and domains
$sourceFilePath = "C:\Users\Name\Documents\Wireshark\unique-ips.txt"
# Read the contents of the input file
$contents = Get-Content -Path $sourceFilePath
# Initialize an empty array to store filtered matches
$filteredMatches = @()
# Define the list of domains and associated IP addresses
$domainIPs = @{
"account-public-service-prod03.ol.epicgames.com" = @("67.202.34.139","54.164.66.255","54.157.123.125","52.205.83.9","52.204.56.84","52.203.65.171","52.0.67.196","44.213.56.223","44.210.17.243","44.207.113.23","35.172.106.180","34.232.183.200","34.225.203.251","34.199.93.64","34.195.107.174","3.92.110.224","3.229.220.193","3.225.60.110","3.225.40.182","3.216.207.164","18.213.90.193","18.211.229.42")
"eos-gateway-ingressv2-prod-c1-w4.befa.live.use1a.on.epicgames.c" = @("44.217.241.174","44.199.125.179","44.196.130.161","34.232.128.104","18.214.111.142","107.20.77.29")
"eos-gateway-ingressv2-prod-c3-w5.befa.live.use1a.on.epicgames.c" = @("54.87.104.91","54.243.92.17","44.211.107.46","35.168.219.102","34.236.78.98","3.210.177.30")
"eulatracking-svc-prod06-pub-1257580502.us-east-1.elb.amazonaws." = @("52.71.213.248","35.173.104.176","35.168.30.157","18.211.121.225")
"fp2e7a.wpc.phicdn.net" = @("192.229.211.108")
"fp3011.wpc.phicdn.net" = @("152.195.50.149")
"priceengine-ecomprod01-pub-2131700027.us-east-1.elb.amazonaws.c" = @("54.156.160.204","50.17.0.218","44.208.219.139","35.170.218.26","34.201.95.44","34.198.192.237")
# "" = @("","")
# "" = @("","")
# "" = @("","")
# "" = @("","")
# "" = @("","")
# Add more domains and IPs as needed
}
# Check each domain and associated IPs
foreach ($domain in $domainIPs.Keys) {
$ips = $domainIPs[$domain]
foreach ($ip in $ips) {
if ($contents -match $ip) {
$filteredMatches += "IP found for ${domain}: ${ip}"
Write-Host "Match found: ${domain} (${ip})"
}
}
}
# Output the filtered matches to a new text file
$filteredMatches | Out-File -FilePath "C:\Users\Name\Documents\Wireshark\egs-filtered-ips.txt"
# Display a message indicating the operation is complete
Write-Host "Filtered matches have been saved to egs-filtered-ips.txt"
One Domain, Three IPs
The results of filtering the IPs through the PowerShell script were very interesting:
IP found for eos-gateway-ingressv2-prod-c1-w4.befa.live.use1a.on.epicgames.c: 44.199.125.179
IP found for eos-gateway-ingressv2-prod-c3-w5.befa.live.use1a.on.epicgames.c: 54.243.92.17
IP found for eulatracking-svc-prod06-pub-1257580502.us-east-1.elb.amazonaws.: 35.168.30.157
IP found for fp3011.wpc.phicdn.net: 152.195.50.149
IP found for priceengine-ecomprod01-pub-2131700027.us-east-1.elb.amazonaws.c: 35.170.218.26
IP found for fp2e7a.wpc.phicdn.net: 192.229.211.108
IP found for account-public-service-prod03.ol.epicgames.com: 52.205.83.9
IP found for account-public-service-prod03.ol.epicgames.com: 52.0.67.196
IP found for account-public-service-prod03.ol.epicgames.com: 34.232.183.200
That's right - the analysis I did last week was of one third of the traffic associated with the Epic Games Store public account service!
The lesson here is to scrape all your target IPs before you start analyzing.
Take Two
Having spilled spaghetti in front of the whole world, it's time to reexamine that traffic in light of this new information.
Following the procedure I used to undertake the first analysis, I generated a new PCAP that only contained the target IPs, using the following filter: (ip.addr == 52.205.83.9) || (ip.addr == 52.0.67.196) || (ip.addr == 34.232.183.200)
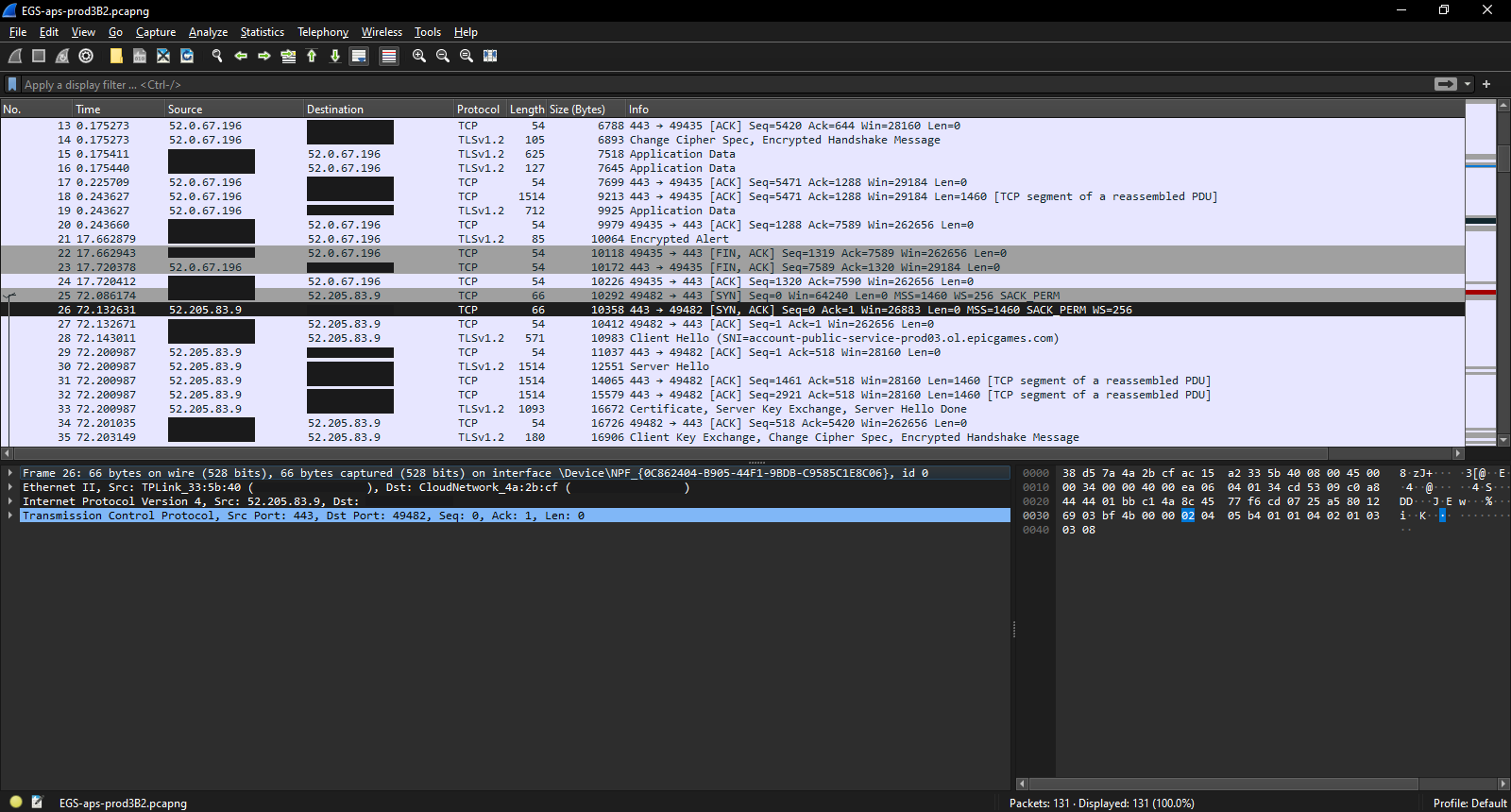
This generated a 131 packet capture, which generally didn't have anything new in the TCP stream. But looking at the actual packets did provide some interesting data.
What appears to be happening is that after getting the initial certificate, an encrypted alert is passed on to the server, possibly confirming receipt of the data. This then triggers the client to end the connection to the first IP address.
Then the client begins the three way handshake with the server at the second IP address. Once that's completed, the new server initiates a certificate and server key exchange.

The network traffic here is a bit more interesting. For some reason, the connection resets after an encrypted alert, at which point, the client connects to the third IP address.
It's unclear why the connection would reset, especially since I don't have anyway to execute TLS inspection, but it does stick out like a thumb compared the rest of the traffic. (Possible reasons include: the general awfulness of Spectrum internet, my internet being disrupted by software updates on the Raspberry Pi I use to host Pi-Hole, any kind of service disruption on Amazon's end.)
Examining the packet further just shows a standard FIN exchange after exchanging data.
The time gap in switching between the first two IPS seems to point towards the possibility that it related to switching between EGS proper and the Unreal. But without the ability to inspect the unencrypted packets, it's hard to be sure what the traffic represents.

