Cybersecurity Project: Epic Games Store Packet Capture - Domains
Last time, I managed to get Epic Games Store mostly functioning in Sandboxie-Plus and analyzed a number of DNS queries for potential suspicious behavior.
Now, I'll be looking at IP addresses for host machines obtained during the packet capture session.
Wireshark Weakness: Resolved Addresses Exporting
Wireshark has many great network capture analysis features, but they're not perfect. For example, Resolved Addresses generates a list of IP/MAC addresses and domain/devices names associated with those addresses.
What it does not do, for some reason, is provide a method of exporting this list from the graphical user interface. Using the command line is necessary for this task, which is a shame, because this feature is ideal for helping develop PiHole blocklists.
So this forced me to take multiple screen captures at the time of capture, then transfer the PCAP to a separate computer for analysis. (My gaming rig is not really setup for that.)
After several rounds of iteration, I discovered that there's no easy way to dump the information via command line - for some reason, every source and destination IP would be the EGS host and the PiHole I use for DNS filtering. This is despite Wireshark correctly displaying IP addresses from outside my network.
I also discovered that I could copy and paste data from the GUI's Resolved Addresses pane... one entry at a time. By that I mean, I can highlight one piece of data, copy it, and paste it. Attempting to copy multiple pieces of data, like all the IP addresses, just results in pasting one IP address.
Analyzing Domains and IPs
After spending an annoying amount of time manually copy-pasting domains and IP addresses into a text document, I began running them through VirusTotal and AlienVault OTX.
After crosschecking their answers on a few easily discernable legitimate domains, I began feeding domains I was less certain about into those sites.
These are the entries that aroused the most suspicion in me, for various reasons:
account-public-service-prod03.ol.epicgames.com
Security vendors' analysis
CyRadar: MaliciousIndicator Facts
2 malicious files communicatingRunning webserver
Resolves to 8 IPs
Present in Umbrella
Present in Majestic
Present in AkamaiAntivirus Detections
Backdoor:Win32/Tofsee.T, TEL:Trojan:Win64/GoCLR.MR!MTB
AV Detection Ratio: 2 / 2Associated Files
Sep 19, 2021 8e7c791dd2a860fb8ff4630b4079351d9865c73316d3071664a8cab86737e890 TEL:Trojan:Win64/GoCLR.MR!MTBAug 31, 2019 b81db9595e7cdc16ca6f106f5610e4442cbaf9049940938b34ce759a42688dfa Win32:BackdoorX-gen\ [Trj] Win.Trojan.Tofsee-6840338-0 Backdoor:Win32/Tofsee.T
Given that Epic Games Store is roughly 5.5 years old, the fact that a Trojan/backdoor was identified on the platform in 2019 definitely raised an eyebrow. However, the fact that only two detections have been made in that time span suggests to me that these were probably not done by Epic. However, this domain is definitely going to be looked at in more depth later.
eos-gateway-ingressv2-prod-c1-w4.befa.live.use1a.on.epicgames.c
No results on VirusTotal/AlienVaulteos-gateway-ingressv2-prod-c3-w5.befa.live.use1a.on.epicgames.c
No results on VirusTotal/AlienVaulteulatracking-svc-prod06-pub-1257580502.us-east-1.elb.amazonaws.
No results on VirusTotal/AlienVault
These are suspicious due to not having any results on VirusTotal and AlienVault, although looking up their IPs suggest they're run out of the same AWS data center that a lot of EGS's services are. (And possibly my cybersecurity course too!)
Also, I'm very curious to see what I can find out about the End User License Agreement traffic.
fp2e7a.wpc.phicdn.net
Fake Update Utilizes New IDAT Loader To Execute StealC and Lumma Infostealers - according to source ArcSight Threat Intelligence - 8 months ago
Contextual Indicators: The domain is popular in the world Contextual Indicators: The domain’s Cisco Umbrella rank is 709 Created On: 2014:11:14 00:00:00VirusTotal Link: https://www.virustotal.com/gui/domain/fp2e7a.wpc.phicdn.net/detection Classification Description: Legitimate website which does not serve any malicious purpose.
ArcSight Threat Intelligence: Suspicious
Antivirus Detections
Trojan:Win32/Prepscram
AV Detection Ratio: 12 / 13Jul 23, 2023 bc0e2cba3466c7b53635df6057dc87bcf622d0439ae766a71b49eae726226507 Win.Malware.Zusy-9957983-0 Trojan:Win32/Prepscram
Multiple Prepscam detections with different hashes
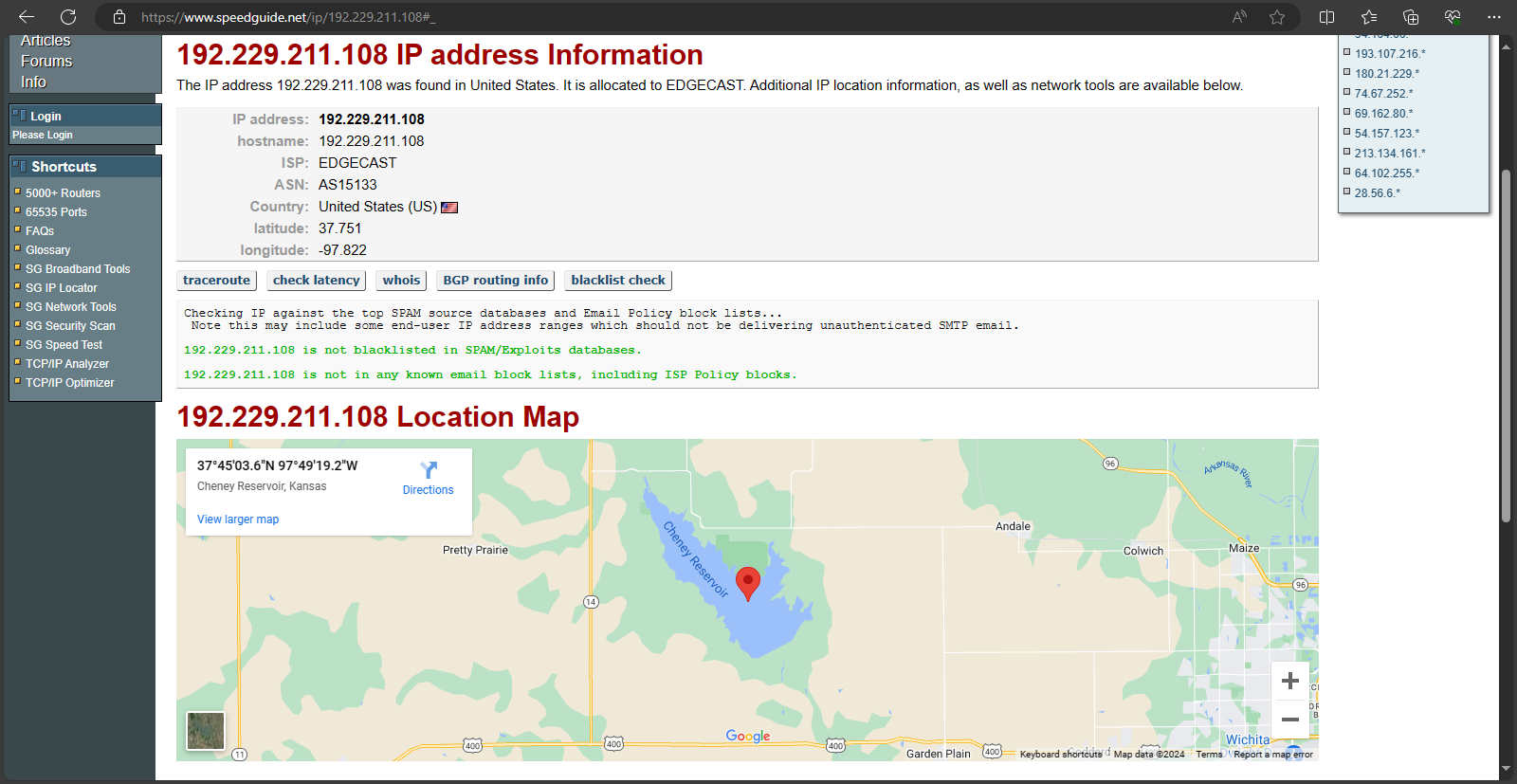
This obviously set off a number of red flags for me, especially considering how recent the latest detection. I immediately popped the IP address into the same website that I'd used to verify the location and ownership of the others, and got this in return:
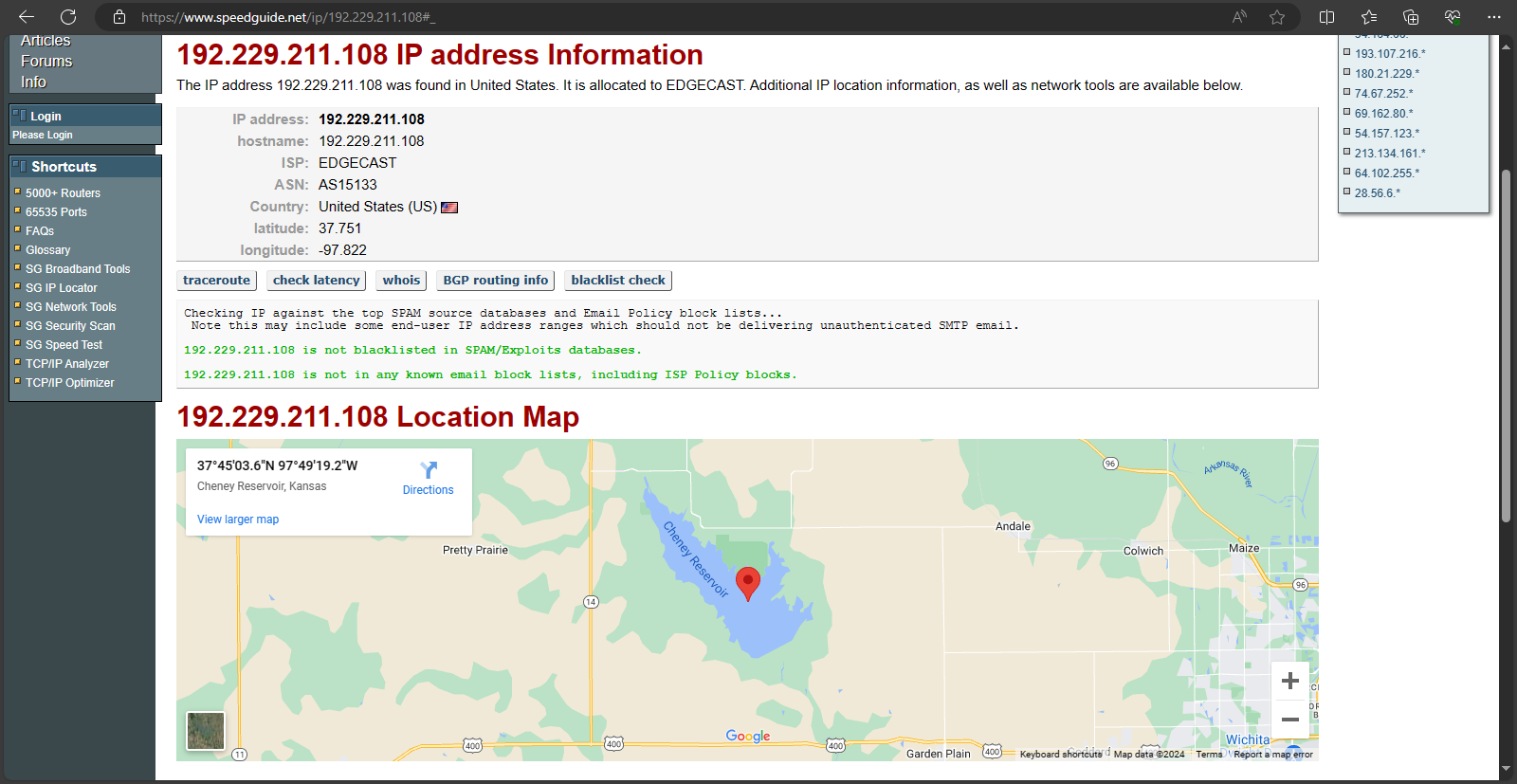
There's a word for an IP address being geolocated in the middle of a reservoir in Kansas:

Now, there's a totally credible explanation for this type of result. Some server clusters are actually put inside specialized containers and immersed in large bodies of water for cooling purposes.
Looking into things further, I discovered that the *.phicdn.netdomain is associated with ocsp.digicert.com, which checks for certificate revocation.
Why they would use this domain, which is suspiciously generic and hosted in a suspicious location, is a question for more experienced investigators.
The final interesting domain I found was this one:
priceengine-ecomprod01-pub-2131700027.us-east-1.elb.amazonaws.c
No results on VirusTotal/AlienVault
This one is pretty easy to understand, but it'll be interesting to see what price data is being moved through this connection.
The Next Steps
With a specific number of interesting domains and IPs to examine, the next step is examine the actual network data flows. The logical place to start is with account-public-service-prod03.ol.epicgames.com, one of Epic Games' domains that has been compromised in the past.
Once we take a look at that one, we'll go through the rest of the ones I've highlighted in this article. Will we find anything interesting? Let's find out!