Cybersecurity Headache: Home Router UXUI

As an aspiring cybersecurity professional, there's all sorts of projects that I could undertake. Maintaining my Pi-Hole DNS black hole is one of those. Personally, I like projects where I'm doing something that has practical benefit to me.
So when I came into some pretty powerful PC hardware, I saw an opportunity.
What I wanted to do:
- Build a system with a Ryzen 7800X3D CPU and RX 7900 XTX GPU
- Set up a Windows VM on the 7800X3D/7900 XTX system
- Place the Windows VM on a subnet
- Install Epic Games Store on the Windows VM
- Use Wireshark to track what traffic EGS produces
- Place an old PC on the same subnet
- Remotely operate the VM through the old PC
What could go wrong?
Problem #1 - Can I Even Subnet?
My network uses TP-Link routers... which means I have to use an app to access an online account to set my router settings.
This is suboptimal from a security perspective for many reasons. Perhaps the biggest one is that you need internet access to set up a LAN.
But setting that aside, there's one major problem - there's no way to actually set up subnets and VLANs. What you do get? IoT Network and Device Isolation options.
What you get with these options are the ability to create a "dedicated wireless network to manage your IoT devices together", or "Isolate devices to protect your network from security threats."
Device isolation seemed to be the right pick, so I set a static IP on the old PC and added it to the Device Isolation list.
Problem #2 - Can't Connect to the Internet
After configuring things, I immediately tested the network connection on the old PC. My first step was opening the browser and checking the default home page links. When this failed, I tried to ping the DNS server... which also failed.
At the same time, the PC was having weird connectivity issues while in isolation mode, with the WiFi dropping periodically.
To troubleshoot this, I did several things:
- Checked to see if find any data in the TP-Link app about what settings Device Isolation uses.
- There wasn't any data, which is a big YIKES.
- Disabled the Device Isolation, checked the ipconfig, re-enabled Device Isolation, and checked ipconfig again.
- Since I had static IP on the old PC, this didn't do anything. More on that later.
- I tried to setup up static routing.
- This apparently applied to the entire network, and when I undid it, I had to reset the router to get any connectivity to the network. Fun!
This experimentation was all necessary because of the following problem:
Problem #3 - Insufficient Documentation
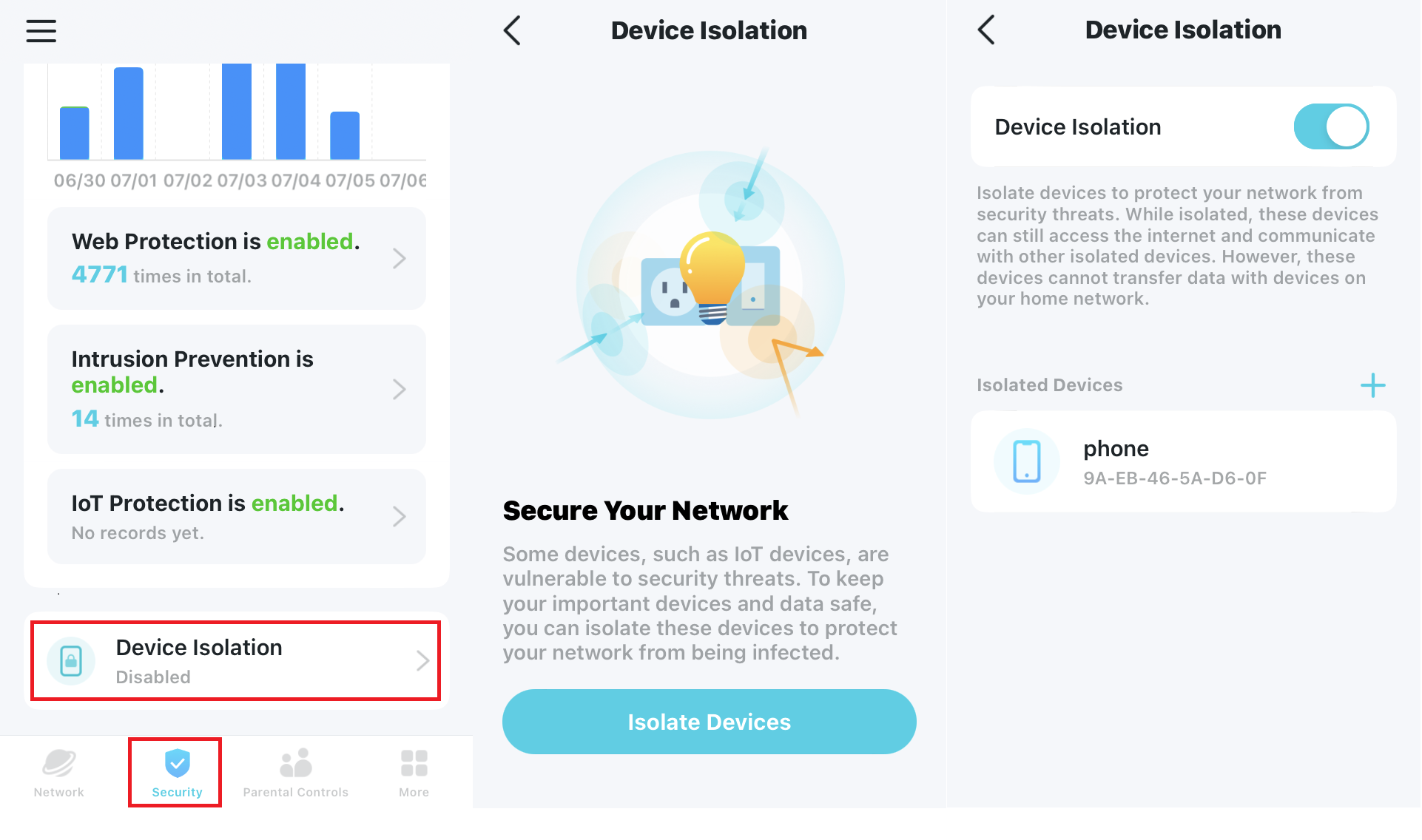
The reason I had so many problems is because, as you can see above, the UI doesn't provide a lot of details.
This might be forgivable if the website was full of detailed documentation. THIS is what they give you - a pretty good explanation of how it works and how to set up Device Isolation. It does not tell you anything about how to troubleshoot issues, and the forums are not helpful either.
One of the big problems with cybersecurity is that building the mindset to be a good practioner is a lot easier when you do it all the time. And that includes the home environment.
The biggest hurdle to that process is that doing cybersecurity properly requires the ability to troubleshoot and fix problems. And if you're not experienced or working with an unfamiliar system, troubleshooting tends to require documentation to explain what to do and what to look for. So the absence of said documentation has a massive negative impact.
Especially when the TP-Link app actually has an entire suite of useful testing/security tools:
- Speed Test
- Detect Cameras
- Scan For Devices
- Ping Test
- Public IP Lookup
- MAC Lookup
- Open Port Checker
- Wi-Fi Interference
None of these were useful for diagnosing the problems, for reasons I will explain below.
Solving the Problem
Because I did have experience with troubleshooting, I eventually figured out the problem.
So what was the solution?
- Remove the static IP address assignment for the old PC.
- Connect the device to a network extension instead of directly to the router, solving the connection issues.
- Activate device isolation.
- Check the ipconfig.
- Check to see if webpages load.
This worked, but I discovered something odd. When I checked the device list in the TP-Link app, the device IP address was this:
###.###.##.55When I checked the results of ipconfig on the system, the result was this:
IPv4 Address: ###.###.##.100 (Preferred)From what I can tell, it seems as though the router assigns IPv4 addresses starting from 100 to isolated devices, but I cannot confirm this until I try to isolate the VM.
Curiously, there's no actual way to check what the Device Isolation IPs are in the app, and the old PC entry on the device list disappeared after closing and reopening the app.
Checking PiHole for DNS queries from the old PC did yield results, so that confirmed that there was proper routing and filtering.
Thankfully, the problem had a simple solution, but that still took a few hours of research and iteration.
What TP-Link Can Do
There's a few things that can be done about this:
- Include IP addresses on Device Isolation device cards.
- Have a Device Isolation troubleshooting page/section that informs users to not try to reserve IP addresses to isolated devices.
- Have an HTTP control panel that allows for detailed control, like older/Netgear routers.
Should they do these things? If they care about the user's cybersecurity, then the answer is yes. Will they do it?
Two of these items are definitely going to be budget and effort sinks, which means that they're unlikely to happen without a lot of motivation to do so.
But it's genuinely confusing that the app's information on isolated devices doesn't include the assigned IP. This is a fairly simple bit of data to expose to the user, and definitely necessary for troubleshooting.
That said, TP-Link continues development of their firmware and app, so perhaps they will address these issues in the near future. One can only hope, because making cybersecurity as easy as possible is a great thing for everyone.

